Validated Products Authorised by Vendors or Third Party Auditors
The easiest way to comply with the Visa and MasterCard security requirements is to use validated products (card readers, terminals, Electronic Cash Registers, etc.) that cannot release or do not handle cardholder data. PNC and our members, in collaboration with product vendors, have listed the products that have been validated to fulfil all necessary security requirements.
The products that have been validated by vendors and/or independent third-party auditors are found in the lists below.
All upgraded software versions must be listed. If you as vendor cannot find your product or software version on the list below, please go to Validation.
Please note: As a merchant, your payment solution also has to comply with the specific requirements of your acquiring company (usually your bank). Please contact your acquirer or payment service provider for further assistance regarding specific technical or security requirements.

-
Terminals and Electronic Cash Registers
-
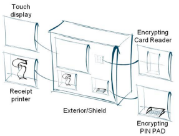
Unattended Payment Terminals
-
Security Design for Terminals

- Terminals that cannot release cardholder data (E2EE)
- Electronic Cash Registers that do not handle any cardholder data (No cardholder data handling)
- Global Point to Point Encrypted solutions – Terminals and Electronic Cash Registers that cannot release cardholder data (P2PE).
For more information on Point to Point Encrypted solutions,
see PCI Security Standard Council webpage
Products on the PCI P2PE list has been approved to handle card holder date according to the PCI standard. However, products on list 1, list 2 and P2PE lists are the acquirers preferred option as they are the easiest way to comply with the Visa and Mastercard security requirements
- Secure terminal components for unattended environments (E2EE)
- UPT Software that do not handle any cardholder data. (No cardholder data handling)
- Secure exterior shield (Exterior shield)
- Terminals, encrypting PIN pads and encrypting card readers that have been validated to fulfil the Security Design requirements (Security Design)